Graphical method helps plan security vulnerability analyses of transportation activities
Graphical method helps plan security vulnerability analyses of transportation activities
The value chain for any given chemical or process facility is a complex set of activities involving the company and its fixed manufacturing sites, as well as various shippers and their transportation and storage facilities.
Value-chain activities for a typical facility generally consist of multiple pathways for both inbound and outbound materials. These may consist of hundreds or even thousands of individual shipments over a year's time. Performing security vulnerability analyses (SVA) for all of these individual shipments or even pathways in the same manner would be cumbersome and probably waste SVA resources.
This article proposes a method for mapping the various incoming and outgoing material pathways for potential target materials for a fixed facility and then using those results to choose which pathways require unique SVAs, which pathways can be adequately analyzed using generic SVAs, and which pathways require no SVA.
Value-chain activities
The American Chemistry Council defines the value chain of chemical or process facilities as consisting of design, procurement, manufacturing, marketing, distribution, transportation, customer support, use, recycle, and disposal.1
The present discussion, however, will cover those portions of the value chain involving transportation and distribution activities of inbound and outbound materials to and from fixed chemical or process manufacturing sites (including waste disposal). Those portions of the value chain that will not be analyzed deal with design, manufacturing and operations, marketing, and customer support.
Transportation and distribution on the value chain include receipt of feed materials by multiple modes of transportation, including ship, barge, rail, truck, air, and pipeline; and distribution of products and waste materials by multiple modes of transportation, including ship or barge, rail, truck, air, and pipeline.
Distribution of materials from fixed sites may include transportation of products directly to a customer, possible interim storage of products, transfer of products between carriers, transportation of samples to potential customers, tollers, distributors, and packagers.
In addition to a host of possible companies and organizations involved are ownership and regulatory responsibility issues associated with the distribution of chemical products and feed materials. For any given shipment, ownership or custody of the materials may transfer at the originating site, receiving site, or some location in between.
Multiple transfers of custody or ownership may occur for any given shipment. The material is likely to be transported in containers or vehicles owned and operated by companies different from the company that offered the material for transportation (generally the manufacturer or seller).
For feedstock materials, the fixed site manufacturer is the final recipient; transfer of ownership to the manufacturing company that will use the material, however, may have occurred before arrival on site (i.e., FOB at the supplier's facility).
Additionally, distributors, freight forwarders, consignees (receivers of shipment), interim storage operators, re-packagers, and others organizations may be involved with shipments to or from the fixed manufacturing site.
Because transportation and distribution of hazardous materials are somewhat varied and complex, determining which segments of the transportation and distribution network for a chemical company's feed and product materials require an SVA is a daunting task, as well as assigning responsibility for the SVA.
SVA in process industries
Many companies have already performed SVAs of fixed facilities to comply with government regulations (e.g., 33 CFR 105 – Marine Transportation Security Act regulations; CFR = Code of Federal Regulations), or as part of voluntary efforts, such as the ACC's security code.
Several different methodologies are available and have been used for these studies, including the CCPS SVA methodology,2 API/NPRA SVA methodology,3 Sandia Vulnerability Analysis Method (VAM),4 as well as several company-specific variants of these SVA methodologies. These studies have been performed on fixed manufacturing sites and are typically limited to the following four types of possible malicious events:
1. Loss of containment of hazardous chemicals on the plant site from intentional damage of equipment or the malicious release of chemicals, which may cause multiple casualties, severe damage, and public or environmental impact.
2. The theft or diversion of materials with the intent to cause severe harm offsite at another location. This includes materials that are severe marine pollutants, known or suspected chemical weapons precursors, radioactive materials, as well as toxic or flammable materials that could be released directly at some offsite location.
3. Contamination or spoilage of materials used in retail food, pharmaceutical, or personal care products to cause public harm onsite or offsite.
4. Degradation of assets or infrastructure or the business function or value of the facility or the entire company where the facility or company is a vital national economic, public welfare, or defense asset in and of itself.
These studies have surveyed and screened the fixed site assets and identified targets of concern based on the hazards should the asset be intentionally abused and the attractiveness of the assets and the site. Many materials have been screened out as being of little use or attractiveness to terrorists, either because their volume was very low (e.g., drum or lab quantities) or because their vapor pressure is so low as to make them unattractive as candidates for release.
Except for situations in which the volume of individual large shipments of a toxic or flammable material are subdivided at a number of sites (a rare occurrence), the individual shipments of materials would be subject to the same screening results as at the fixed sites.
For example, a material that is held in large volume at a site but whose vapor pressure does facilitate the formation of a large vapor cloud (e.g., weak hydrochloric acid) could be screened out. So too would a tank truck of the same material en route to a fixed site.
Therefore, the fixed sites can be treated as nodes where the hazardous materials that are worthy of analysis in the value chain have already been defined. This assumes that an SVA has already been performed for the fixed sites where the inbound materials are received and the products are manufactured.
Therefore, the fixed site SVA is used to determine which transportation and distribution pathways in the value chain are worthy of concern. For example, if a material has been screened out in the fixed-site SVA as being an unattractive target, perhaps because of its small volume received on site, then an SVA in the transportation network of similar volumes of the same materials would be unnecessary, unless a more serious risk exists in the value chain and the company has taken ownership or is the shipper of record where the higher risk exists.
In general, the following types of materials are targets on site and would also be targets in the transportation and distribution network:
- Toxic materials with high vapor pressures in volumes large enough to cause adverse health effects beyond the area directly adjacent to the release. Note: the more remote the shipments (i.e., the farther from large population densities), the more mass of the material that can be tolerated if released.
In general, quantities less than 1,000 lb will not cause widespread health effects. This is equivalent to about three to four 55-gal drums of most chemicals. This would also include waste materials.
- Flammable materials, particularly light hydrocarbons that can create an energetic vapor cloud explosion when ignited in air. As stated above, a single truck load of a material like LPG may not be an attractive target at relatively remote or large-area fixed site but may be a very attractive target while passing through a highway tunnel en route to the same site. This would also include waste materials.
- Known or suspected chemical weapons precursors, in any quantity (a conservative assumption, but prudent until more is known about the quantity, purity, and manufacturing methods for the actual chemical weapons). This would include site products that are shipped as samples.
Note that the management of filling sample orders is sometimes out-sourced to third-party companies. These sample clearinghouse companies were established to make it easier for potential customers to obtain small amounts of products to perform testing.
The security rules followed by these sample clearinghouse companies are crucial to keeping samples of target chemicals (e.g., chemical weapon precursors) out of the hands of possible adversaries.
- Materials in bulk quantities (i.e., tank truck shipments) that are classified by the US Department of Transportation as severe marine pollutants.6
- Radioactive materials in any quantity. Although the individual source sizes used in most industrial applications of radioactive materials are very low (about 30-50 millicuries), they are small, easily portable, and easily pilferable while in transit and can be combined with similar materials stolen from other sites or shipments to create even a small "dirty bomb."
Of course, sources used in radiographic non-destructive tests are much larger and represent significant hazards by themselves.
- Products that are used in food, pharmaceutical, or personal care products in the retail market, in bulk shipment quantities. These can be contaminated in transit and could be used to produce retail products that can quickly expose many thousands of people before they are quarantined. Small shipments or sample shipments of these materials are not likely targets in the transportation and distribution network.
Mapping activities
The pathways associated with the incoming and outgoing materials of concern can be shown diagrammatically with appropriate notations for shipper, interim storage, change in ownership or shipper of record and other important information that describes the pathway. It is important to ensure that all assets and materials identified in the fixed-facility SVA as attractive and high-risk targets be depicted, including samples, chemical weapons precursors, disposal of wastes as applicable.
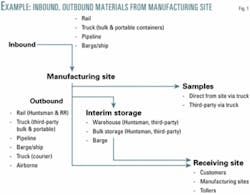
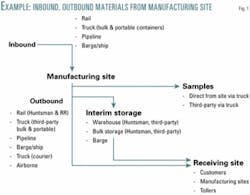
Fig. 1 shows an example of the inbound material pathways for a notional facility.
The nature of the chemical hazard and how it is distributed are both important considerations for value-chain SVAs, whereas for fixed sites, the mere presence of certain materials on site is the key issue. Materials that may have been screened-out as not being a viable target on site may offer an attractive and viable target in the transportation network.
For example, flammable materials in a remote site many not be regarded as targets, but if the shipments must pass through densely populated areas or adjacent other public and attractive targets, the same material may be highly attractive en route.
In addition to the properties of the materials describe above, the mapping of each inbound and outbound material should also be characterized for its transportation characteristics to help prioritize the pathways identified.
These characteristics are:
- Transportation mode(s), pattern, and routing, including origin, destination, and intermediate stops or transfers.
- Number of containers (e.g., rail cars) per shipment.
- Volume per container.
- Number of trips per unit time.
- Predictability of shipments.
- Number and sizes of population centers along the route.
- Very dense population areas along the route ("hot-spots").
- Proximity to significant landmarks.
- Proximity to public venues (e.g., a large stadium).
- Storage in transit (rail yards, leased track, warehouse).
- Transportation equipment design and special features.
- Operating and security procedures for parties in value chain.
- Sensitive end-uses or processing locations.
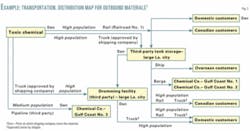
An examination of the results of mapping the incoming materials at the site (Fig. 2) and the outgoing materials in the site (Fig. 3) reveal the following:
- The site in Fig. 2 reveals that there are nine pathways associated with the delivery of ammonia, chlorine, and propylene to the site. Of these, five are fixed transportation assets: pipelines and the salt dome storage facility. The remainder are mobile assets (truck and rail).
- The site in Fig. 3 reveals that there are 12 pathways associated with the delivery of the toxic product to various customers. Of these, three are fixed transportation assets: a pipeline, third-party tank farm, and the third-party drumming facility. The remainder are mobile assets and include rail, truck, barge, and ship.
There could be some disagreement whether a pipeline system is a mobile or fixed asset. The US Department of Transportation regulates pipelines in the US and pipeline companies are considered carriers as defined in 49 CFR 171.
For the purposes of performing SVAs on pipelines, however, they will be considered fixed assets. This is because from a security and vulnerability standpoint they do not move. Like mobile assets, however, an aboveground pipeline segment passing through a large city or over a river is a more attractive than a remote, buried segment of the same pipeline.
In Fig. 3, the salt dome storage facility and the receiving company-owned pipeline SVAs would certainly be the responsibility of the company receiving the propylene because it is owned by the receiving company.
The third-party pipeline, however, the pipeline owned by the oil company, as well as the truck and rail shipments of propylene, ammonia, and chlorine utilize assets owned and operated by other firms. In Fig. 3, none of the transportation assets that carry the toxic product is owned or operated by the producing company. All are third-party assets.
In determining who is best suited to analyze the threats and vulnerabilities involved with transportation assets, some important questions will arise:
- Do shipments legally become the property of a carrier (e.g., a railroad) en route? Or, do they remain the property of the shipper?
- Where does that transfer of property occur?
- Who is the shipper of record?
- Are there multiple transfers of property ownership?
Determining SVA activities
Once the mapping is complete, an SVA should be performed for each identified pathway. It may not be the responsibility of the fixed site, however, to perform all of these analyses. Some recommendations:
- The fixed manufacturing site company should perform unique SVAs for the fixed portions of the transportation and distribution network that it owns itself in the relevant pathways, such as warehouses, terminals, pumping stations, pipelines, and docks.
It is assumed that any portions of the marine transportation system will be analyzed separately as part of the facility Security Assessment and Facility Security Plan pursuant to the MTSA regulations, 33 CFR 105.
- For fixed portions of each pathway where the physical infrastructure is not owned by the fixed site company, confirmation that the owner of the infrastructure has performed (or will perform) an SVA of the relevant assets and pathways should be made.
For example, a third-party pipeline company that ships products or feed materials for many companies should analyze its own pipeline system. This would also apply to the fixed portions of railroads and their operations, including track routings and any interim storage in yards en route.
In this respect a railroad is much like a pipeline, where there is fixed infrastructure that supports movement of materials along (or through) it.
- For mobile portions of each pathway where the physical infrastructure is not owned by the fixed site company, confirmation that the owner of the infrastructure has performed (or will perform) an SVA of the relevant assets or pathways should be made.
For example, a trucking company that routinely delivers feed materials to a fixed manufacturing site should be responsible for SVAs of its own equipment, routes, personnel, and operations. This would apply to railroad equipment (the trains themselves), trucking companies, courier companies (e.g., Federal Express, UPS, etc.), barge companies, and shipping companies.
- For mobile portions of each pathway where the transportation infrastructure is owned by the fixed manufacturing site company, that company should perform the SVA of those assets or pathways: for example, if the fixed site company operates its own trucking fleet to deliver products.
If ownership of the materials or containers transfers to the fixed site company at the originating or interim location along a pathway (i.e., FOB at the shipper's location), there may be some negotiation with the carrier or interim-storage location owner with respect to completion of the SVA.
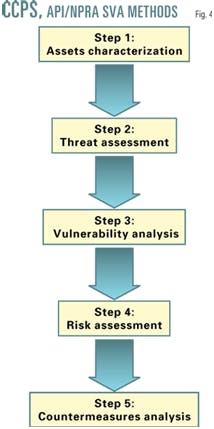
Existing SVA methodologies can be easily adapted to the analysis of the transportation and distribution portion of the value chain, particularly those methodologies that are designed to general SVA techniques.
For example, both the CCPS and API/NPRA SVA methods share a common analytical design that is not specific to any type of asset or target. Although they were originally developed for fixed sites, the thought process is generic. Fig. 4 shows a simplified flow chart for these SVA methods.
For fixed portions of the transportation and distribution infrastructure (e.g., warehouses, terminals, etc.), these methodologies and those similar to them can be used, as they exist in accordance with the guidance published by their sponsors. For mobile assets, the analytical process embodied in these methods will require slight adaptation as follows:
- Targets: Inbound or outbound shipments of toxics, flammables, CWPs, or pollutants, attractiveness factors may change en route; use the maximum target attractiveness identified along the pathway.
- Threats: Theft, truckjacking, piracy, and other threats specific to the transportation and distribution environment.
- Vulnerabilities: Use of mobile containers for transport as weapons themselves, product contamination or tampering en route, disruption of vital transportation networks, nodes, and capability; and evaluation of existing security transportation equipment or route security countermeasures. The ACC Transportation Security Guidelines and Security Code Implementation Guidelines provide additional guidance on analyzing the vulnerabilities of transportation systems.1 5
In assessing the vulnerabilities of value chain activities related to transportation, the ACC recommends that the following transportation issues be examined:
—Degree of access to shipment.
—Degree of attendance to shipment during movement, interim storage, layover, pickup, or transfer points.
—Visibility and location of shipments.
—Predictability of shipment movement.
—Special procedures or controls employed, e.g., GPS tracking, communication, leak detection, or theft detection.
- Special equipment design, e.g., anti-theft systems, valve protection, tamperproof seals
- Improved countermeasures: Recommendations for transportation and distribution security countermeasures; References 1, 5, and 7-10 provide examples of published sources of security measure recommendations.
Although an SVA should be performed for each pathway, it is acceptable to perform common or generic SVAs for pathways with the same mode of transportation and handling the same type of material.
For example, it may be acceptable to perform only one SVA of incoming toxic materials via truck, one SVA of incoming toxic materials via rail car, etc. This generic SVA would serve as a model for all pathways involving the same type of material and mode of transportation and would be compared to pathway-specific conditions and adjustments made as necessary.
Care must be exercised, however, in applying generic SVAs. Even though several pathways may share the same mode of transportation and the same type of material, the risks and target attractiveness may vary substantially between the pathways.
For example, the same material and mode of transportation passing through a large metropolitan area would represent a more attractive target than the same combination that occurs only in remote areas. In such cases the generic SVA does generally not have to be completely re-performed as a unique study for the two pathways but must be modified to accommodate these varying risks.
Other resources
In addition to general SVA methods such as CCPS and API/NPRA, there are several specialized vulnerability-assessment methodologies published recently that were developed specifically to transportation activities.
- US Department of Transportation, Surface Transportation Vulnerability Assessment.7 This study uses a target-threat-vulnerability-risk ranking-countermeasures analytical process that is very similar to the CCPS and API/NPRA methods.
- American Association of State Highway and Transportation Officials, Security Task Force, A Guide to Highway Vulnerability Assessment for Critical Asset Identification & Protection.8 This study also uses a target-threat-vulnerability-risk ranking-countermeasures analytical process that is very similar to the CCPS and API/NPRA methods but has been prepared specifically to analyze the security status of highway systems.
- Transportation Security Administration, Transportation Risk Assessment and Vulnerability Evaluation (TRAVEL) Method.9 This study also uses a target-threat-vulnerability-risk ranking-countermeasures analytical process that is very similar to the CCPS and API/NPRA methods and was created to give the TSA itself a common vulnerability assessment methodology for its work.
- Transportation Security Administration, TSA Self-Assessment Risk Module (TSARM).10 This TSA method is more fixed in that it does not have the same open thought process as the above methods. When the user enters a scenario by answering general questions about target attractiveness, consequence, economic impact, loss of functions, etc., the method provides suggested pre-defined countermeasures.
These are:
Note that access to this methodology is limited to companies that own assets that they desire to analyze. For example, TSA will not release it to consultants.
- API Pipeline SVA example. This published example by the American Petroleum Institute applies the API/NPRA SVA methodology specifically to pipeline systems.
References
1. Transportation Security Guidelines for the U.S. Chemical Industry, American Chemistry Council, et al, December 2001.
2. Guidelines for Analyzing and Managing the Security Vulnerabilities of Fixed Chemical Sites, American Institute of Chemical Engineers/Center for Chemical Process Safety, August 2002.
3. Security Vulnerability Assessment Methodology for the Petroleum and Petrochemical Industries, American Petroleum Institute/National Petrochemical Refiners Association, May 2003.
4. Chemical Facility Vulnerability Assessment Methodology, US Department of Justice/Sandia National Laboratories, July 2002.
5. Implementation Resource Guide for Responsible Care Security Code of Management Practices: Value Chain Activities, American Chemistry Council, September 2002.
6. 49 CFR 172.101, Hazardous Materials Table, US Department of Transportation.
7. Surface Transportation Vulnerability Assessment, US Department of Transportation, Research and Special Programs Administration, October 2001.
8. A Guide to Highway Vulnerability Assessment for Critical Asset Identification & Protection, American Association of State Highway and Transportation Officials, Security Task Force, May 2002.
9. TRAVEL Users Manual, Transportation Security Administration, Version 2.
10. TSA Self-Assessment Risk Module (TSARM), Transportation Security Administration.
Based on a presentation to the 19th Annual Center for Chemical Process Safety International Conference (AIChE), Orlando, June 29-July 1, 2004.
The authors
Michael J. Hazzan (mhazzan@ acutech-consulting.com) is manager for the eastern business unit at Acutech Consulting Group, Lawrenceville, NJ. He has also served as a consulting engineer in process safety and process security for 25 years. He holds an engineering degree from the US Naval Academy, is a member of the AIChE and the American Society of Safety Engineers, and is a registered professional engineer in New Jersey, Pennsylvania, Missouri, and Texas.
Irene Jones (irene_jones@ huntsman.com) is manager of process safety at Huntsman Chemical Co., Houston. She has also served as EHS-related positions at Texaco Chemical Co. Jones holds a BS in chemistry from SUNY-Buffalo and is a member of the American Chemical Society.